"Last year was by far the worst ever for security, with 2,164 incidents that exposed 822 million records, according to one security report." 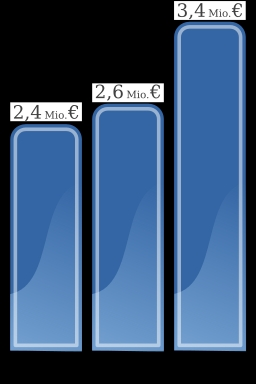
In his recent ITWorldCanada article this is only one of many striking comments made by author Andrew Brooks. He goes on in the article to outline nine key etiquette steps which can help you protect your reputation even if a breach occurs. Some are obvious, such as disclose what has happened and what is at risk, as well as focusing on looking after your customers and any others who may be affected by the breach.
The natural tendency in these situations is to try to 'protect your backside' and to listen to those who counsel that you not admit to what has happened in the face of potential legal issues. This is a tendency that can get you into trouble. Face up to the issue, honestly tell people what you know and also what you don't know and then focus on correcting what went wrong. Your customers depend upon your actions in this case.
If you look at the recent Heartbleed problems most organizations survived this issue with no major consequences because steps were taken quickly to fix the issue on their sites and the major software vendors dealt with its impacts on their packages quickly. The information came out broadly and those who might be at risk were advised on what to do to safe guard their logins etc.
In a related article in ITWorldCanada, the same author documents that one of the reasons that such breaches might be growing is the increasing use of the cloud as a tool of IT systems. He outlines the results of a research study that was undertaken with a survey of IT professionals which indicated that increased use of cloud applications could lead to a tripling of the potential for a security breach. The case may not be linear but certainly it is sensible to think that with more external data, applications and use of the same there is more potential risk. Part of the problem is many cloud solutions do not disclose very well what security of data they have in place.
The estimated cost of a security breach is as much as $200 per record especially with larger enterprise level data stores. The unfortunate part is that in many cases all of the necessary information on how the security of the application structure is formulated is not visible to the IT professionals running the corporate network. If this is the case for larger networks with full scale professional IT management, then it is even a greater risk for smaller networks operated by part time or non IT professionals.
Unfortunately, it appears that as more data is collected by organizations, the potential issues associated with the data are going to increase over time. Each new high profile data breach leads to a lessening of the confidence of consumers that their information will be well protected. This can lead to issues for both those needing the data to carry out their work and for those who wish to make use of the services being offered. The costs of recovery and mitigation end up being born by all.
As data structures are better understood by business leaders the need for secure management of ALL electronic data whether on your own network or being supported in cloud services will become more of a priority in business planning.
The consequences of a breach, even a fairly small one, can be disastrous for a business if not handled well. The ideas that Andrew has put forward for action after the fact are fine, but the real solution is to fully understand your situation and how steps have been put in place to protect your data at all times.
Avoidance of the breach is the best result that any business can achieve. Look at the design and management structures you have in place for all data usage and storage. Ask the questions before there is a problem. You will be happy you did.
How is your data secured? Are protocols for security declared by your cloud suppliers? Are they there for your protection or for theirs? Are you aware?
Lee K
Photo credit: Wikimedia Commons Public Domain, German Data Losses 2008-2010